Monthly Archives: noviembre 2023
Tree Based Machine Learning Algorithms
Machine Learning Algorithms: How They Work and Why They Matter by Endra 𝐀𝐈 𝐦𝐨𝐧𝐤𝐬 𝐢𝐨 Feb, 2024
In this case, it is often like the algorithm is trying to break code like the Enigma machine but without the human mind directly involved but rather a machine. Since the data is known, the learning is, therefore, supervised, i.e., directed into successful execution. The input data goes through the Machine Learning algorithm and is used to train the model. Once the model is trained based on the known data, you can use unknown data into the model and get a new response. Discover the fundamental concepts driving machine learning by learning the top 10 algorithms, such as linear regression, decision trees, and neural networks. Reinforcement Learning is a type of machine learning algorithms where an agent learns to make successive decisions by interacting with its surroundings.
Testing involves evaluating the performance of the algorithm on a separate set of data. Gradient boosting algorithms employ an ensemble method, which means they create a series of «weak» models that are iteratively improved upon to form a strong predictive model. The iterative process gradually reduces the errors made by the models, leading to the generation of an optimal and accurate final model. In simple terms, linear regression takes a set of data points with known input and output values and finds the line that best fits those points.
Instead of explicitly telling the computer what to do, we provide it with a large amount of data and let it discover patterns, relationships, and insights on its own. Machine learning algorithms are only continuing to gain ground in fields like finance, hospitality, retail, healthcare, and software (of course). You can foun additiona information about ai customer service and artificial intelligence and NLP. They deliver data-driven insights, help automate processes and save time, and perform more accurately than humans ever could. Decision tree, also known as classification and regression tree (CART), is a supervised learning algorithm that works great on text classification problems because it can show similarities and differences on a hyper minute level.
Types of Machine Learning Techniques
Training data being known or unknown data to develop the final Machine Learning algorithm. The type of training data input does impact the algorithm, and that concept will be covered further momentarily. Machine Learning is, undoubtedly, one of the most exciting subsets of Artificial Intelligence. It completes the task of learning from data with specific inputs to the machine. It’s important to understand what makes Machine Learning work and, thus, how it can be used in the future. The concept of machine learning has been around for a long time (think of the World War II Enigma Machine, for example).
Or, in the case of classification, we can train the network on a labeled data set in order to classify the samples in the data set into different categories. All of these innovations are the product of deep learning and artificial neural networks. Machine Learning is complex, which is why it has been divided into two primary areas, supervised learning and unsupervised learning.
Artificial intelligence is a general term that refers to techniques that enable computers to mimic human behavior. Machine learning represents a set of algorithms trained on data that make all of this possible. Machine learning algorithms are becoming increasingly important in today’s digital world, powering everything from image recognition to natural language processing. In this article, we’ll delve into the process of how machine learning algorithms are developed, trained, and deployed. Classification is regarded as a supervised learning method in machine learning, referring to a problem of predictive modeling as well, where a class label is predicted for a given example [41].
Features are the individual measurable characteristics or attributes of the data relevant to the task. For example, in a spam email detection system, features could include the presence of specific keywords or the length of the email. Labels, on the other hand, represent the desired output or outcome for a given set of features. In the case of spam detection, the label could be «spam» or «not spam» for each email. Here, the model, drawing from everything it learned, is queried about something not included in the training data.
Learn Latest Tutorials
Some of the familiar types of regression algorithms are linear, polynomial, lasso and ridge regression, etc., which are explained briefly in the following. Thus, the key contribution of this study is explaining the principles and potentiality of different machine learning techniques, and their applicability in various real-world application areas mentioned earlier. Machine learning can be classified into supervised, unsupervised, and reinforcement. In supervised learning, the machine learning model is trained on labeled data, meaning the input data is already marked with the correct output. In unsupervised learning, the model is trained on unlabeled data and learns to identify patterns and structures in the data.
- With such a wide range of applications, it’s not surprising that the global machine learning market is projected to grow from $21.7 billion in 2022 to $209.91 billion by 2029, according to Fortune Business Insights [1].
- It works by finding the directions in the data that contain the most variation, and then projecting the data onto those directions.
- The analogy to deep learning is that the rocket engine is the deep learning models and the fuel is the huge amounts of data we can feed to these algorithms.
The broad range of techniques ML encompasses enables software applications to improve their performance over time. In common usage, the terms “machine learning” and “artificial intelligence” are often used interchangeably with one another due to the prevalence of machine learning for AI purposes in the world today. While AI refers to the general attempt to create machines capable of human-like cognitive abilities, machine learning specifically refers to the use of algorithms and data sets to do so.
Linear regression is a supervised machine learning technique used for predicting and forecasting values that fall within a continuous range, such as sales numbers or housing prices. It is a technique derived from statistics and is commonly used to establish a relationship between an input variable (X) and an output variable (Y) that can be represented by a straight line. You also need to know about the different types of machine learning — supervised, unsupervised, and reinforcement learning, and the different algorithms and techniques used for each kind. A support vector machine (SVM) is a supervised machine learning model used to solve two-group classification models.
The input layer has the same number of neurons as there are entries in the vector x. At the majority of synapses, signals cross from the axon of one neuron to the dendrite of another. All neurons are electrically excitable due to the maintenance of voltage gradients in their membranes.
In addition to these most common deep learning methods discussed above, several other deep learning approaches [96] exist in the area for various purposes. For instance, the self-organizing map (SOM) [58] uses unsupervised learning to represent the high-dimensional data by a 2D grid map, thus achieving dimensionality reduction. The autoencoder (AE) [15] is another learning technique that is widely used for dimensionality reduction as well and feature extraction in unsupervised learning tasks. Restricted Boltzmann machines (RBM) [46] can be used for dimensionality reduction, classification, regression, collaborative filtering, feature learning, and topic modeling. A deep belief network (DBN) is typically composed of simple, unsupervised networks such as restricted Boltzmann machines (RBMs) or autoencoders, and a backpropagation neural network (BPNN) [123]. A generative adversarial network (GAN) [39] is a form of the network for deep learning that can generate data with characteristics close to the actual data input.
In general, the effectiveness and the efficiency of a machine learning solution depend on the nature and characteristics of data and the performance of the learning algorithms. Besides, deep learning originated from the artificial neural network that can be used to intelligently analyze data, which is known as part of a wider family of machine learning approaches [96]. Thus, selecting a proper learning algorithm that is suitable for the target application in a particular domain is challenging. The reason is that the purpose of different learning algorithms is different, even the outcome of different learning algorithms in a similar category may vary depending on the data characteristics [106]. To intelligently analyze these data and develop the corresponding smart and automated applications, the knowledge of artificial intelligence (AI), particularly, machine learning (ML) is the key.
Decision TreesDecision trees are a popular algorithm used for classification tasks, such as identifying whether an email is spam or not. They work by recursively splitting the data into subsets based on the most important features. Decision trees are commonly used in marketing, fraud detection, and healthcare. Features are the characteristics of the data that the algorithm will use to make predictions or decisions.
Neural networks are behind all of these deep learning applications and technologies. Random forests are a type of ensemble learning method that employs a set of decision trees to make predictions by aggregating predictions from individual trees. Reinforcement learning (RL) is a machine learning technique that allows an agent to learn by trial and error in an interactive environment using input from its actions and experiences. Unlike supervised learning, which is based on given sample data or examples, the RL method is based on interacting with the environment. The problem to be solved in reinforcement learning (RL) is defined as a Markov Decision Process (MDP) [86], i.e., all about sequentially making decisions. An RL problem typically includes four elements such as Agent, Environment, Rewards, and Policy.
Transfer learning is currently very common because it can train deep neural networks with comparatively low data, which is typically the re-use of a new problem with a pre-trained model [124]. A brief discussion of these artificial neural networks (ANN) and deep learning (DL) models are summarized in our earlier paper Sarker et al. [96]. Examples of notable are random forests, Gradient Boosting techniques and decision trees, using recursive binary split based on criteria like Gini impurity or information gain etc. In this paper, we have conducted a comprehensive overview of machine learning algorithms for intelligent data analysis and applications. According to our goal, we have briefly discussed how various types of machine learning methods can be used for making solutions to various real-world issues.
What is Deep Learning and How Does It Works [Updated] – Simplilearn
What is Deep Learning and How Does It Works [Updated].
Posted: Tue, 29 Aug 2023 07:00:00 GMT [source]
In this tutorial, we will be exploring the fundamentals of Machine Learning, including the different types of algorithms, training processes, and evaluation methods. By understanding how Machine Learning works, we can gain insights into its potential and use it effectively for solving real-world problems. Gini impurity is a measure of the lack of homogeneity in a dataset which specifically calculates the probability of misclassifying an instance chosen uniformly at random.
The primary distinction between the selection and extraction of features is that the “feature selection” keeps a subset of the original features [97], while “feature extraction” creates brand new ones [98]. Cluster analysis, also known as clustering, is an unsupervised machine learning technique for identifying and grouping related data points in large datasets without concern for the specific outcome. It does grouping a collection of objects in such a way that objects in the same category, called a cluster, are in some sense more similar to each other than objects in other groups [41]. It is often used as a data analysis technique to discover interesting trends or patterns in data, e.g., groups of consumers based on their behavior. In a broad range of application areas, such as cybersecurity, e-commerce, mobile data processing, health analytics, user modeling and behavioral analytics, clustering can be used.
“Flat” here refers to the fact these algorithms cannot normally be applied directly to the raw data (such as .csv, images, text, etc.). This means that they are fed large amounts of data, which they use to identify patterns and relationships. Once the algorithm has identified these patterns, it can make predictions or decisions based on new data that it hasn’t seen before. In supervised learning, data scientists supply algorithms with labeled training data and define the variables they want the algorithm to assess for correlations. Both the input and output of the algorithm are specified in supervised learning.
AI, which originally referred to human-like intelligence in machines, now refers to any aspect of technology that partially shares attributes with human intelligence. There are various types of neural networks beyond classic examples, including convolutional neural networks, recurrent neural networks (RNNs) like long short-term memory networks (LSTMs), and more recently, transformer networks. Deep learning relates to neural networks, with the term “deep” referring to the number of layers inside the network.
To become proficient in machine learning, you may need to master fundamental mathematical and statistical concepts, such as linear algebra, calculus, probability, and statistics. You’ll also need some programming experience, preferably in languages like Python, R, or MATLAB, which are commonly used in machine learning. Once the algorithm identifies k clusters and has allocated every data point to the nearest cluster, the geometric cluster center (or centroid) is initialized. First, the dataset is shuffled, then K data points are randomly selected for the centroids without replacement. In the below, we’ll use tags “red” and “blue,” with data features “X” and “Y.” The classifier is trained to place red or blue on the X/Y axis.
To start your own training, you might consider taking Andrew Ng’s beginner-friendly Machine Learning Specialisation on Coursera to master fundamental AI concepts and develop practical machine learning skills. DeepLearning.AI’s Deep Learning Specialisation, meanwhile, introduces course takers to how to build and train deep neural networks. For example, a business how does machine learning algorithms work might feed an unsupervised learning algorithm unlabelled customer data to segment its target market. Once they have established a clear customer segmentation, the business could use this data to direct future marketing efforts, like social media marketing. A K-nearest neighbour is a supervised learning algorithm for classification and predictive modelling.
Many clustering algorithms have been proposed with the ability to grouping data in machine learning and data science literature [41, 125]. In the following, we summarize the popular methods that are used widely in various application areas. Usually, the availability of data is considered as the key to construct a machine learning model or data-driven real-world systems [103, 105].
Machine learning for Java developers: Algorithms for machine learning – InfoWorld
Machine learning for Java developers: Algorithms for machine learning.
Posted: Wed, 24 Jan 2024 08:00:00 GMT [source]
The Apriori algorithm was initially proposed in the early 1990s as a way to discover association rules between item sets. It is commonly used in pattern recognition and prediction tasks, such as understanding a consumer’s likelihood of purchasing one product after buying another. K-nearest neighbors or “k-NN” is a pattern recognition algorithm that uses training datasets to find the k closest related members in future examples. In the field of NLP, improved algorithms and infrastructure will give rise to more fluent conversational AI, more versatile ML models capable of adapting to new tasks and customized language models fine-tuned to business needs. Determine what data is necessary to build the model and whether it’s in shape for model ingestion.

Machine learning algorithms are trained to find relationships and patterns in data. Naive Bayes is a set of supervised learning algorithms used to create predictive models for either binary or multi-classification. Based on Bayes’ theorem, Naive Bayes operates on conditional probabilities, which are independent of one another but indicate the likelihood of a classification based on their combined factors. The first one, supervised learning, involves learning that explicitly maps the input to the output. Other types of training include unsupervised learning, where the patterns are not labeled, and reinforcement learning.
The goal now is to repeatedly update the weight parameter until we reach the optimal value for that particular weight. The y-axis is the loss value, which depends on the difference between the label and the prediction, and thus the network parameters — in this case, the one weight w. With the input vector x and the weight matrix W connecting the two neuron layers, we compute the dot product between the vector x and the matrix W. The typical neural network architecture consists of several layers; we call the first one the input layer. The rapid evolution in Machine Learning (ML) has caused a subsequent rise in the use cases, demands, and the sheer importance of ML in modern life.
Data can be of various forms, such as structured, semi-structured, or unstructured [41, 72]. Besides, the “metadata” is another type that typically represents data about the data. We live in the age of data, where everything around us is connected to a data source, and everything in our lives is digitally recorded [21, 103]. The data can be structured, semi-structured, or unstructured, discussed briefly in Sect.
- Learn more about this exciting technology, how it works, and the major types powering the services and applications we rely on every day.
- In unsupervised learning, the model is trained on unlabeled data and learns to identify patterns and structures in the data.
- Given training data and a particular task such as classification of numbers, we are looking for certain set weights that allow the neural network to perform the classification.
- It is also beneficial to put theory into practice by working on real-world problems and projects and collaborating with other learners and practitioners in the field.
- Machine learning’s ability to extract patterns and insights from vast data sets has become a competitive differentiator in fields ranging from finance and retail to healthcare and scientific discovery.
While each of these factors is independent, the algorithm would note the likelihood of an object being a particular plant using the combined factors. Each time we update the weights, we move down the negative gradient towards the optimal weights. This tangent points toward the highest rate of increase of the loss function and the corresponding weight parameters on the x-axis. In the end, we get 8, which gives us the value of the slope or the tangent of the loss function for the corresponding point on the x-axis, at which point our initial weight lies. These numerical values are the weights that tell us how strongly these neurons are connected with each other.
What’s An Automated Market Maker Amm? Amms Defined
This model additionally makes it easier for crypto holders to earn rewards by joining a liquidity pool. The pricing mechanism in AMMs, while usually efficient, in some instances may lead to points like impermanent loss for liquidity providers, particularly in extremely volatile market conditions. These pools, full of different tokens, adjust prices dynamically according to the altering ratios of belongings. This system ensures that the pricing is reflective of present market circumstances, driven by supply and demand throughout the pool. Both classes use non-custodial good contracts, and a deterministic pricing rule is carried out between two or extra pools of tokens.
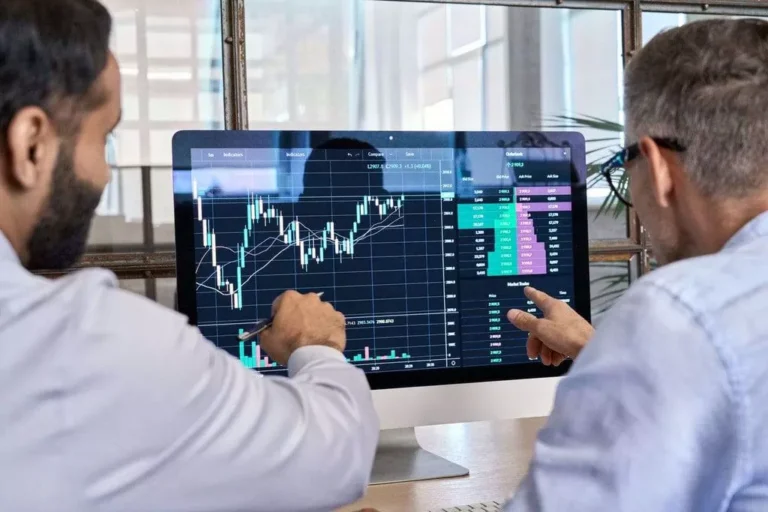
Traditional exchanges rely on liquidity from their very own reserves or from a person market maker to execute orders. AMMs as a substitute rely on liquidity that is sourced from different users and pooled together, an idea known as a liquidity pool. In liquidity swimming pools, liquidity providers “lock” equal quantities of two or extra tokens into a smart contract for use as liquidity for trades from different customers. AMMs have turn into the primary way to commerce tokens throughout the DeFi ecosystem, and tons of use a formula called “constant product market maker” to maintain the prices of tokens traded in liquidity pools fixed. These AMM exchanges are primarily based on a relentless operate, the place the mixed asset reserves of buying and selling pairs should stay unchanged. In non-custodial AMMs, person deposits for buying and selling pairs are pooled inside a smart contract that any dealer can use for token swap liquidity.
Hybrid Operate Market Maker (hfmm)
Users are incentivized to lock their tokens in liquidity swimming pools by getting paid out a share of the trading charges generated by that device, proportional to how a lot they’ve contributed. On the opposite hand, AMMs use good contracts to automate the swapping of assets, making them cheaper and environment friendly compared to traditional exchanges. For example, Curve AMMs—known because the stableswap invariant—combine both a CPMM and CSMM using a sophisticated formulation to create denser pockets of liquidity that convey down worth impact inside a given range of trades.
Chainalysis reported that DEFI accounted for $2.3bn of crypto-related crime in 2021. Those DEX which are built on layer 2 Ethereum functions – like Metis or Arbitrum – are popular because of the cheaper fees and ease of bridging from Ethereum though there are some important drawbacks. The Market Depth metric is usually described as the quantity required to maneuver the worth +/-2%. The larger that quantity the higher confidence you can have that your trade won’t transfer the value away from your desired entry or exit. DEX’s are a core component of DEFI – decentralised finance – generating 24hr buying and selling quantity in extra of $2bn, in accordance with Coingecko.
This mannequin can supply more flexibility and higher capital efficiency for multi-asset pools. In exchange, LPs receive LP tokens, which can fluctuate in value based on the buying and selling activity and the general performance of the liquidity pool. Unlike traditional market-making mechanisms, which depend on order books and human market makers to perform trades, AMMs make use of a singular algorithmic method. As a outcome, for this mannequin to work, token A and token B need to be provided in the right ratio by liquidity providers, and the quantity of liquidity should be adequate. The strategy of earning rewards by providing liquidity is also called liquidity mining or yield farming. AMMs could make use of off-chain sources like worth oracles to supply dependable value discovery and capital effectivity.
Exterior Worth Sources
Price discovery in Automated Market Makers (AMMs) differs basically from traditional financial markets. In AMMs, costs usually are not set via an order guide however are decided algorithmically based mostly on the assets in the liquidity swimming pools. In return, they obtain liquidity tokens, which represent their share of the pool. AMMs set the prices of digital assets and provide liquidity in the type of liquidity swimming pools. Automated market makers (AMMs) have emerged as a preferred various to conventional order book-based exchanges for cryptocurrency buying and selling.

In this article, we will give you an summary of how AMMs work, explore the assorted forms of AMMs, and highlight their respective professionals and cons. Balancer offers multi-asset pools to extend exposure to totally different crypto belongings and deepen liquidity. With centralized exchanges, a purchaser can see all of the asks, corresponding to the prices at which sellers are willing to sell a given cryptocurrency. While this presents more options for a purchaser to buy crypto belongings, the ready time for an ideal match may be too long for their liking.
What’s The Best Automated Crypto Trading Platform?
These swimming pools facilitate trading by automatically executing trades based mostly on preset algorithms, embodying what does AMM stand for. This innovation has considerably broadened the scope of DeFi (Decentralized Finance), allowing for more accessible, environment friendly, and safe trading within the crypto ecosystem. Different forms of AMM fashions include fixed product, fixed sum, and hybrid pools. As our article exhibits, automated market makers have established themselves as an integral part within the DeFi group. Various models are used and the approaching years will show which protocols are the most effective. Through oracles, DEXs also can concentrate liquidity inside these worth ranges and improve capital efficiency.
AMMs are algorithmic protocols that remove intermediaries from the market-making process. DEXs use AMM algorithms to confirm crypto transfers between traders without utilizing orderbooks or centralized market makers. Instead, AMM DEXs use sensible contracts to confirm P2P crypto transfers between traders. All the transfers on AMM DEXs happen on blockchains with good contract functionality, together with Ethereum, Cardano, and Solana. On the other hand, exchanges make positive that counterparties are available for all trades.
Because AMMs are a new model of a conventional practice called «market making,» reviewing how market making works on CEXs and contrasting it with DeFi helps to make clear the perform of AMMs. The trajectory of AMMs factors towards an revolutionary financial https://www.xcritical.com/ future where trading is extra inclusive, decentralized, and pushed by superior technologies. Provides straightforward and open entry to liquidity and buying and selling, making it user-friendly for a large viewers.
The aim of PMMs is to make sure that the prices on these platforms reflect what’s occurring within the wider financial market. Token T acts as a decentralized exchange medium between the reserves of token A and token B. In the TSMM or Token Swap model, the swapping between two tokens is finished with the assistance of an middleman token. This model is implemented together with the token swap mannequin in Bancor V2 protocol. This model is just like the CPMM, however the multiplication within the method is changed with addition.
In this state of affairs, the liquidity providers take up the position of market makers who’re required to supply liquidity for trading pairs. At its core, an Automated Market Maker is an algorithmic protocol that permits the autonomous and continuous buying and selling of digital belongings with out the necessity for traditional market-making mechanisms. Unlike the standard order guide mannequin utilized in traditional finance, the place buyers and sellers place orders, AMMs rely amm in crypto on liquidity pools to facilitate buying and selling. In this situation, AMM liquidity providers haven’t any control over which price factors are being offered to merchants, leading some folks to check with AMMs as “lazy liquidity” that’s underutilized and poorly provisioned. Meanwhile, market makers on order guide exchanges can control precisely the worth factors at which they need to purchase and promote tokens.
- Also, as a substitute of utilizing dedicated market makers, anybody can participate to supply liquidity to these swimming pools by depositing each belongings represented in the pool.
- This is creating a far more competitive marketplace for liquidity provision and will doubtless result in greater segmentation of DEXs.
- The result’s a hyperbola (blue line) that returns a linear change rate for giant elements of the worth curve and exponential prices when trade rates close to the outer bounds.
- This automation eliminates the necessity for intermediaries, making the process more environment friendly.
Liquidity swimming pools ensure that there are all the time belongings out there for trading, whatever the time or market conditions. Unlike traditional exchanges that rely on particular buyers and sellers, AMMs allow users to trade instantly, 24/7. Also aiming to increase liquidity on its protocol, DODO is using a model generally recognized as a proactive market maker (PMM) that mimics the human market-making behaviors of a traditional central limit order book. The protocol uses globally accurate market prices from Chainlink Price Feeds to proactively move the value curve of every asset in response to market changes, growing the liquidity close to the present market worth. Ultimately, this facilitates extra environment friendly trading and reduces the impairment loss for liquidity providers.
Traditional markets often have excessive barriers to entry, limiting participation to well-established businesses and financial institutions. However, with AMMs, individuals can contribute their tokens to liquidity pools and earn fees, providing them with an opportunity to participate in the market and generate passive earnings. Furthermore, the use of automated market makers eliminates the necessity for order books, making trading more efficient and less susceptible to manipulation. This accessibility and efficiency have allowed for faster adoption of DEXes, providing customers with greater management over their belongings.

In distinction, AMMs, prevalent in DeFi, use algorithms to set prices and facilitate trades. Early AMM models usually face challenges in efficiently utilizing the capital in liquidity swimming pools. Risk of losses for liquidity providers when the worth of deposited assets changes unfavorably. One important risk is impermanent loss, which happens when the worth of tokens in a pool adjustments compared to after they had been deposited. Liquidity pools are on the heart of AMM platforms like WhiteSwap, functioning as the core mechanism that allows these automated cash makers to facilitate trading by offering liquidity.

These protocols enable crypto individuals to freely swap all kinds of cryptocurrency tokens. Liquidity swimming pools are a giant pile of funds that traders can trade in opposition to and liquidity suppliers are those that add funds to liquidity pools. In return for offering liquidity to the protocol, Liquidity suppliers earn fees from the trades that take place in their pool. AMMs’ algorithmic protocols and liquidity swimming pools have replaced traditional order e-book fashions, providing a decentralized and efficient trading expertise. While AMMs include sure challenges and limitations, their advantages outweigh these issues, making them an important component of the DeFi ecosystem. By contributing funds, liquidity providers earn a share of buying and selling fees generated by transactions throughout the pool proportionate to the total liquidity they supply.
A DeFi App can implement one type of AMM mannequin or a mixture of a number of AMM fashions. Impermanent loss happens when the prices of two belongings in a liquidity pool change, inflicting the worth of 1 asset to extend while the opposite decreases. By using synthetic property, customers make all their trades with out counting on their underlying digital belongings, making monetary products attainable in DeFi, including futures, choices, and prediction markets.
Industrial Automation Software Testing Options
Automation will enable builders to self-provision the sources and companies they should develop and deploy software program. Make positive it really works with cellular devices so users can access and monitor on the go, growing flexibility and response to operational necessities. Use predictive analytics to foresee potential issues to develop proactive upkeep plans and scale back operational downtime. Whether you’re navigating the complexities of AI-driven automation, integrating robotics seamlessly, or diving into the world of sensible manufacturing, Matellio stands ready custom industrial software development to remodel your manufacturing facility into a tech-driven powerhouse. Automation ensures that your trade sources, including raw materials and energy, are used effectively, minimizing waste and maximizing total resource utilization. This ongoing analysis helps you modify your automation method and keep it in sync together with your evolving objectives, guaranteeing maximum benefits.
Companies can improve overall gear performance and operational continuity by decreasing downtime by automating maintenance and fault detection operations. The software’s real-time monitoring and reporting options enable firms to act rapidly and decisively by providing them with up-to-date operational knowledge. Create automation logic, combine hardware parts, and develop any needed user interfaces. Also, integrate different modules or parts of the software to ensure they work seamlessly collectively.

The conceptual thought is realized at this point and turns into a workable industrial automation system. Industrial automation software program solutions require scalable infrastructure and storage options, which cloud integration services offers. It is a vital part of up to date industrial automation, enabling distant entry, real-time information processing, and cross-border collaboration.
As the demands on software growth grow, so does the need for methods to enhance its efficiency. Safety is ensured by way of rigorous testing, adherence to industry standards, and implementing fail-safeness and redundancies. Security involves encrypting knowledge, securing community connections, and regularly updating software to protect against cyber threats.
Faster Time-to-market
Therefore, you can reduce the danger of deployment-related issues like downtime or data loss. Tools like Ansible can streamline this task, guaranteeing that your software transitions to production smoothly. Tools like GitHub Copilot and Tabnine offer multilingual assist, making them invaluable for generating boilerplate code, design patterns, and extra, based on the descriptions you provide.

It’s not just about utilizing machines; it’s a sensible way of doing every little thing from creating merchandise to placing them together and delivering them. The production lines operate with flawless synchronization, where downtime becomes a distant memory, and where every piece of equipment works in perfect concord. Factory automation software is a game-changer that’s not simply in demand; but becoming the heartbeat of sensible manufacturing. They got here to us with their best folks to attempt to understand our context, our business concept, and developed the first prototype with us. I assume, with out ELEKS it in all probability wouldn’t have been potential to have such a profitable product in such a short time frame. There are several actions that could trigger this block together with submitting a sure word or phrase, a SQL command or malformed knowledge.
Low stage sensors and actuators are most probably developed with C and C++, whereas higher layers are applied with Java or C#. Connectivity provides complexity with multiple elements using totally different protocols to propagate messages up to the tip consumer. Parasoft supplies testing tools to deal with each layer of complexity, seamlessly built-in with refined reporting and analytics to assist organizations handle this growing complexity. To ensure a unified and efficient process, reduce set up disruptions by integrating your custom industrial automation design software with legacy equipment and techniques. Cybersecurity measures play a major role in the robustness of commercial automation design software.
Address At Present’s Fashionable Software Growth Challenges
This might contain putting in software on machines, configuring hardware components, and making certain every thing is prepared for use. Provide coaching to end-users and relevant personnel to ensure they are comfy with the brand new automation system. The integration of robotics, controlled by automation software program, is extensively used in duties corresponding to welding, painting, and material handling. This enhances precision, reduces labor costs, and improves security in manufacturing environments.
- Training consists of greedy the basics of automation, mastering the chosen tools, and studying finest practices.
- HMI design is the process of making user-friendly and intuitive interfaces that may talk info, instructions, and feedback to the person.
- Creating and configuring the mandatory software setting is a critical step in software growth.
- Our success has gained the long-term trust of probably the most innovative research institutions and sophisticated manufacturing firms.
- After deployment, implement monitoring instruments to maintain track of the system’s efficiency, determine points, and proactively handle potential issues.
- Modern industrial processes are altering at a rate never seen earlier than due to technological breakthroughs.
Traceability reports present clear and full information about the event progress. Teams can easily determine what quantity of requirements had been already applied and the way totally they’re tested. Once you may have an excellent understanding of automation, you can start to automate more complicated tasks. While automation presents numerous value reduction advantages, the beginning value could additionally be high.
Factory Automation Software Program: Use Circumstances
According to a survey, growing effectivity can result in further prospects for company development, which is the first motivation for 57% of companies to deploy automation. Approximately 3.5 million industrial robots are in use worldwide, based on the International Federation of Robotics. The Federation acknowledged that because the epidemic, there was a pointy increase in demand, accounting for a progress price of more than 30% yearly.
In the future, AI and ML are doubtless for use to automate much more duties within the software program growth course of. With cameras and picture processing algorithms, robots can visually evaluate and determine based on pictures which have been acquired, due to machine vision. Precision in industrial processes is ensured by machine vision, which is essential for defect identification, quality management, and visible recognition. Industries with excessive job volumes and standardized processes benefit tremendously from RPA. Connecting devices and machines will allow you to to have real-time monitoring, data collection, and evaluation, thereby enhancing decision-making processes and optimizing operational efficiency in numerous industries.
Functional Security And Security Coding Requirements Compliance
To ensure secure and steady operations, intrusion detection methods, firewalls, and encryption are used to guard sensitive information and important assets. No, Factory Automation could be tailor-made to fit the wants of businesses of all sizes. While massive enterprises typically implement comprehensive automation systems, smaller businesses can undertake scalable options https://www.globalcloudteam.com/ that handle specific pain points in their manufacturing processes. Hyperautomation involves the combination of a number of automation applied sciences, similar to RPA, AI, and course of mining, to create comprehensive and interconnected automated methods. This pattern aims to streamline end-to-end processes and enhance total enterprise operations.
The Internet, while enhancing the flexibility of the techniques, has created an explosion of latest threats and complexities. With any security holes within the control software program, there’s a danger of the gates being opened to a terrorist assault using an unexpected situation in the process. Parasoft C/C++ testing solutions offers probably the most complete software testing resolution for safety available on the market for safety, so organizations can develop and launch software with fewer dangers. In this article, we will discover the tasks that may be automated in a software program improvement process, the future of automation in software program development, and the benefits and challenges of automating software growth. By minimizing the need for manual intervention and dramatically growing overall operational efficiency, industrial automation design software program smoothly automates repetitive processes. Factory Automation Software refers to technology solutions that automate and optimize industrial processes within a producing facility.
Distant Entry And Management
We perceive the frustration and expense that comes from maintaining and running code in declining states of functionality. Over time, a number of influences on your software program may cause it to tackle a lifetime of its own. The design of Parasoft C/C++test CT is specifically designed to integrate into open supply unit testing frameworks like GoogleTest, CppUnit and any other framework. Our team of consultants is raring to listen to your ideas and supply tailor-made solutions to meet your distinctive wants.
Automation streamlines packaging processes by effectively handling, sorting, and packaging merchandise. It ensures uniform packaging requirements, reduces errors, and enhances the pace of the packaging line. From revolutionizing assembly strains to enhancing high quality management, here are the myriad use circumstances that make this know-how the cornerstone of sensible manufacturing. It is extra versatile than mounted automation and can be used to produce a greater variety of merchandise. The equipment is managed by a pc program that can be modified as per different manufacturing necessities.
It involves using numerous tools, together with sensors, robotics, and software, to streamline operations and improve effectivity. RPA is a sort of automation that makes use of software program robots to automate duties that are sometimes performed by people. This can embody issues like knowledge entry, customer service, and financial transactions. RPA is a comparatively new technology, however it is becoming more and more in style as companies search for ways to enhance effectivity and scale back prices. It brings in high-tech instruments like sensors, programmable logic controllers (PLCs), and robots to make sure everything runs easily. The use of machines, robots, and automatic system solutions can obviously add worth and help businesses achieve new ranges of efficiency and productiveness.


Recent Comments